How Linux Kernel Runs Cybersecurity Tools Inside!
Extended Berkeley Packet Filter technology enables programs to run safely within the Linux kernel, revolutionizing cybersecurity. It provides unprecedented visibility into system behavior with minimal overhead, transforming how we detect threats and enforce security policies in cloud environments.
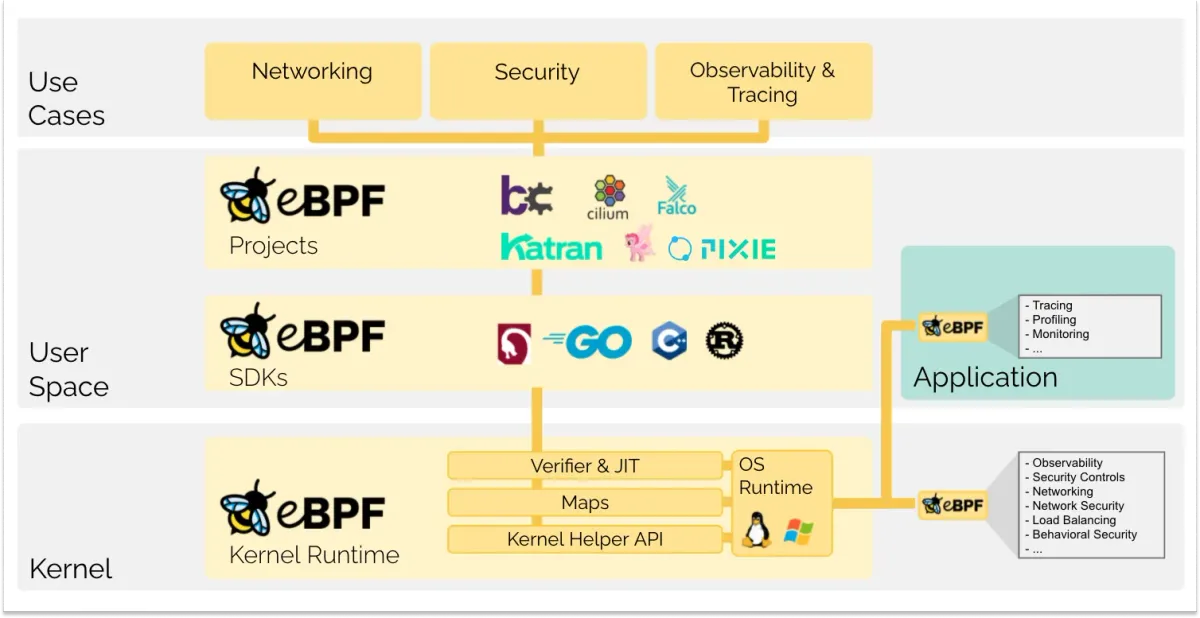
Extended Berkeley Packet Filter (eBPF) represents a fundamental shift in how we approach operating system security. Rather than requiring cumbersome kernel modifications or risky kernel modules, eBPF makes the Linux kernel dynamically programmable at runtime while ensuring its integrity remains intact. This principle solves several key challenges that previously hindered kernel innovation:
Safe OS Customization
By hosting a safe and efficient virtual machine within the kernel, eBPF allows customizing kernel behavior dynamically while achieving performance comparable to native kernel code. The constrained environment and rigorous verification lower the barrier to kernel modifications, significantly reducing the risk of introducing bugs that could lead to service outages.
Rapid Deployment Without Disruption
Changing the kernel traditionally requires rebooting machines, which disrupts workloads and incurs significant operational costs. eBPF programs can be loaded dynamically at runtime, enabling rapid deployment across fleets without service disruptions. This acceleration dramatically shortens the feedback loop for testing and qualifying security enhancements.
Integration with Existing Kernel Components
While eBPF programs attach to the kernel to introduce alternative behavior, they can also safely interact with existing kernel state. Programs can fall back to standard kernel processing when they have nothing of interest to handle, creating a flexible model where existing kernel implementations can be leveraged without reimplementing similar functionality.# Cybersecurity Revolution: How eBPF is Transforming Linux Kernel Security
Extended Berkeley Packet Filter (eBPF) represents one of the most significant advancements in Linux kernel technology in recent years, particularly for cybersecurity applications. This powerful framework allows developers to run programs directly within the Linux kernel without modifying kernel source code or loading kernel modules, creating new possibilities for security monitoring, threat detection, and infrastructure protection.
What is eBPF?
eBPF evolved from the original Berkeley Packet Filter (BPF), which was created in 1992 as a way to filter network packets. While BPF was limited to packet filtering, eBPF dramatically expands these capabilities to run custom programs triggered by various system events.
At its core, eBPF allows developers to write programs that run in a privileged context within the kernel space. These programs are verified for safety, JIT-compiled for performance, and can attach to various kernel subsystems through hooks called "attach points." This privileged position within the kernel makes eBPF particularly valuable for cybersecurity applications, where visibility into system behavior is paramount.
Unlike popular misconceptions, eBPF's design was not influenced by Classic BPF, and the name was chosen primarily for familiarity. Introduced in kernel 3.18 (released in December 2014), eBPF functions as a safe programmable virtual machine hosted on top of a performant in-kernel runtime. The eBPF virtual machine has a set of 11 registers and a fixed-size stack, with a versatile instruction set including arithmetic operations, load and store instructions, jumps, and atomic operations for safe memory access.
The eBPF Runtime Architecture
The eBPF subsystem within the Linux kernel implements the runtime and defines the system call interface to interact with it. This architecture creates a powerful framework for dynamic kernel programmability while ensuring safety and performance. Key components include:
eBPF Bytecode and Instruction Set
eBPF bytecode is a finite sequence of 64-bit or 128-bit instructions that define the operations performed by eBPF programs. The instruction set closely resembles hardware instruction set architectures (ISAs), which simplifies implementation of interpreters and JIT compilers. This near-equivalence to actual hardware ISAs allows optimizing compiler backends to emit eBPF assembly whose performance approaches natively compiled programs.
Verification Process
The verifier, a crucial security component, inspects bytecode before accepting it into the kernel. It ensures safety properties through a multi-stage process:
- Control-Flow Graph Validation - Analyzes program structure to prevent infinite loops and unreachable code
- Symbolic Execution - Exhaustively explores all execution paths for safety violations
- Post-Verification Optimizations - Performs transformations like dead code elimination
- JIT Compilation - Converts verified bytecode to native machine instructions
Kernel Hooks and Attachment Points
eBPF programs are event-driven, executing when the kernel encounters specific hook points. These hooks exist throughout the kernel for system calls, function entry/exit, network operations, tracepoints, and more. When predefined hooks don't meet requirements, developers can create custom hook points via kernel probes (kprobes) or user probes (uprobes).
Safety Properties and Enforcement
Safety is a critical aspect of eBPF programs. The verifier enforces specific properties to protect the kernel's runtime integrity and uphold invariants of the execution context. These safety guarantees include:
Memory Safety
For all memory regions accessible to the program, the verifier performs precise bounds tracking and ensures no out-of-bounds accesses, invalid or arbitrary memory accesses, or use-after-free errors occur. The verifier rejects any program that could potentially compromise memory safety.
Type Safety
The verifier maintains precise knowledge of the type of each register that points to memory regions. It leverages BTF (BPF Type Format) to capture information about kernel and eBPF program types, ensuring aggregate types like structs aren't accessed beyond allowable limits.
Resource Safety
eBPF programs must release all allocated resources before termination, including memory, acquired locks, and references to kernel objects. The verifier tracks these resources symbolically and verifies their proper release.
Information Leak Prevention
The verifier prevents any kernel information leaks by analyzing pointers to kernel memory. It performs escape analysis to ensure such pointers don't escape into user-accessible memory and blocks attempts to read uninitialized stack regions.
Data Race Freedom and Deadlock Prevention
The verifier ensures a program's access to kernel state is free from data races by enforcing synchronization through helpers. For deadlock prevention, the verifier disallows holding more than one lock at a time.
Real-World Security Applications
The security industry has rapidly adopted eBPF technology to build next-generation security solutions. Notable examples include:
Falco has pioneered runtime security monitoring by using eBPF to detect anomalous behavior within containers and cloud-native environments. Its ability to identify potential security threats with minimal overhead has made it a standard component in many Kubernetes security stacks.
Cilium provides network security for container environments by leveraging eBPF to implement security policies at the application protocol level. This approach offers significantly more context-aware security than traditional IP-based controls, allowing organizations to secure microservices with granular, identity-based policies.
Tracee, developed by Aqua Security, uses eBPF to trace system calls and detect suspicious activities in real-time. It can identify fileless malware, privilege escalation attempts, and container escape techniques that traditional security tools might miss.
Hubble extends Cilium's networking capabilities with security-focused observability features, providing detailed insights into network flows between application components—essential for detecting lateral movement attempts and data exfiltration.
Despite their impressive capabilities, these tools represent just the beginning of what's possible with eBPF security instrumentation. However, adopting these technologies does require navigating certain limitations and challenges.
Challenges and Limitations
Despite its transformative potential, eBPF faces several key challenges in security implementations:
Verifier Scalability
The eBPF verifier performs static analysis to ensure program safety, but faces scalability issues with larger, more complex programs. It struggles with path explosion in programs containing many conditional branches, particularly within loops. When the number of potential execution paths grows exponentially, the verifier may hit its instruction complexity limit and reject valid programs.
Verifier Correctness
The verifier's safety guarantees depend on the correctness of its implementation. Any logical bug in the verification algorithm or failure to account for unsafe behavior in unexplored paths could allow harmful programs to execute. The complexity of the verifier codebase, coupled with frequent changes to support new use cases, makes maintaining correctness increasingly challenging.
Formal Verification
There has been no comprehensive formal investigation of the verifier and whether its safety guarantees are sound. Some promising attempts have been made to formally specify the verifier's numerical abstract domain and verify the C implementation of range analysis logic. However, full formal verification remains an open research challenge due to the verifier's complexity and rapid evolution.
Security Model
The criticality of eBPF bugs affecting kernel integrity has led to restrictions on unprivileged use. Capabilities like CAP_BPF, CAP_NET_ADMIN, and CAP_PERFMON are required for loading various types of eBPF programs. Improving verifier correctness guarantees could potentially enable relaxing these restrictions, making eBPF more useful for unprivileged security applications.
eBPF vs. Traditional Security Approaches
When compared to traditional security methodologies, eBPF-based solutions offer distinct advantages:
Kernel Modules vs. eBPF
Traditional kernel modules provide deep visibility but require continuous maintenance with kernel updates and risk system stability. In contrast, eBPF programs undergo rigorous verification before execution, eliminating the risk of system crashes while still providing kernel-level visibility.
In-Process Agents vs. eBPF
Traditional security agents provide application-level visibility but can be bypassed or disabled by sophisticated attackers. eBPF operates within the kernel itself, making it significantly more resistant to tampering or evasion attempts.
Syscall Tracing vs. eBPF
Traditional tools like ptrace offer behavioral insights but introduce substantial performance overhead—often 20-30% degradation. eBPF's just-in-time compilation and kernel integration reduce this overhead to single-digit percentages while maintaining comprehensive monitoring capabilities.
Performance Impact
The performance advantage of eBPF is particularly significant for security applications. Traditional approaches often force a choice between security coverage and system performance. eBPF breaks this tradeoff by enabling comprehensive security monitoring with minimal overhead, making continuous runtime security practical even in performance-sensitive production environments.
CO-RE and BTF: Making eBPF Practical for Security Teams
Recent advancements in eBPF technology have been particularly significant for security applications. CO-RE (Compile Once, Run Everywhere) and BTF (BPF Type Format) together solve one of the most challenging aspects of deploying eBPF security tools: kernel version compatibility.
CO-RE allows security vendors to compile their eBPF programs once and deploy them across different kernel versions without recompilation. BTF provides rich type information that helps CO-RE relocate field accesses correctly across kernel versions. In practice, this means a security tool can monitor critical kernel structures even as their memory layout changes between kernel versions.
For example, a cloud security provider might develop an eBPF-based container escape detection mechanism. With CO-RE and BTF, they can deploy this protection across customer environments running different Linux distributions and kernel versions without maintaining separate builds for each configuration. A security team can monitor for specific namespace-related system calls regardless of whether the customer is running Ubuntu 20.04, Red Hat Enterprise Linux 8, or a custom kernel—drastically simplifying deployment and maintenance.
The kernel's BTF capabilities extend beyond just CO-RE support. The compact representation (with an order of magnitude reduction in size compared to traditional DWARF debug information) allows it to be included with kernel images by default. This makes BTF information consistently available to the verifier for enhanced type checking and safety enforcement.
As Linux continues to power much of the world's infrastructure, eBPF-based security solutions leveraging these advances are becoming essential for organizations that need to protect increasingly complex and distributed systems without compromising performance.




